Email Spoofing – What Is It? | Its Distinction From Phishing, Etc and Much More - corkerthlent
It is common practise in spoofing and misleading campaigns to disguise the origin of an electronic mail reception as coming from someone or something that the recipient knows or trusts. Sophisticated attacks use email head counterfeit to establish a bogus source address, which is what most recipients consent as true. Without paying strict attention to the header, consumers would erroneously believe the message is coming from a legalise source. People are more inclined to believe anything if it has a well-legendary brand name. Therefore, they're many likely to accept computer virus files, click harmful websites, and fifty-fifty reassign money to a ship's company they've never heard of.
Because of the approach email networks are constructed, email spoofing is a real possibility. When sending emails, the applications programme designates a sender address; the outbound mail providers give no idea if the email is real or faked.
Bad mails whitethorn be detected and filtered with the aid of destination systems and antimalware technology. Sadly, privacy procedures aren't implemented by entirely email providers. Even then, users may tick the email headers attached to each message to see whether the recipient individuality is fake.
Email Spoofing: A Agile Overview
Spoofing has get over a trouble since the late 1960s because the manner mail systems function. Spammers invented it as a way to bypass spam filtering. In the 1890s, the problem grew increasingly widespread, and by the 2000s, it had grown into a major worldwide safety concern.
Postal service faking and fraud was with success combated in 2014 with the introduction of security procedures. Since these measures have been implemented, numerous forged fake emails hold been sent to trash folders or ingest been discarded and never reached the mailboxes of their intended recipients.
Reasons to be concerned about netmail spoofing
Even although many fake emails may Be quickly discovered and fixed by just dismissing the messages, there are others that can create significant issues and represent meaning security threats. Every bit an instance, an email that seems to come up from a well retail site, it English hawthorn solicit the receiver for personal information like a passcode or bank account entropy.
It's also possible that when the consumer clicks on the hyperlink in the counterfeit e-mail that spyware is installed on their system. An example of an organisation emailing violate includes faking messages from Chief Executive or CEO of a firm seeking a money transmit or login for interior access privileges.
Reasons for e-mail spoofing
Assailants utilise faked netmail for a variety of purposes, including phishing.
- Keep the honest user's identity operator hidden.
- Overcome spammers and blocklists and any other security. Cable internet companies and Ip may be blocked to reduce the hazard.
- If you wish sensitive information, appear to be someone you can commi, such arsenic a coworker Beaver State a buddy.
- Become a true institution to gain access to account entropy. One example is playing as a financial services society.
- Perpetrate identification fraud aside posing as a particular individual and seeking sensitive private data from them.
- Negatively impact the recipient's standing in the community of interests.
- Spyware may be launched & disseminated through files that have been secreted.
- Use a world-in-the-intervening hack to baffle access to confidential information between people and organisations.
- Learn third-party vendor-collected sensitive information.
Is there a distinction between spoofing, phishing and domain caricature?
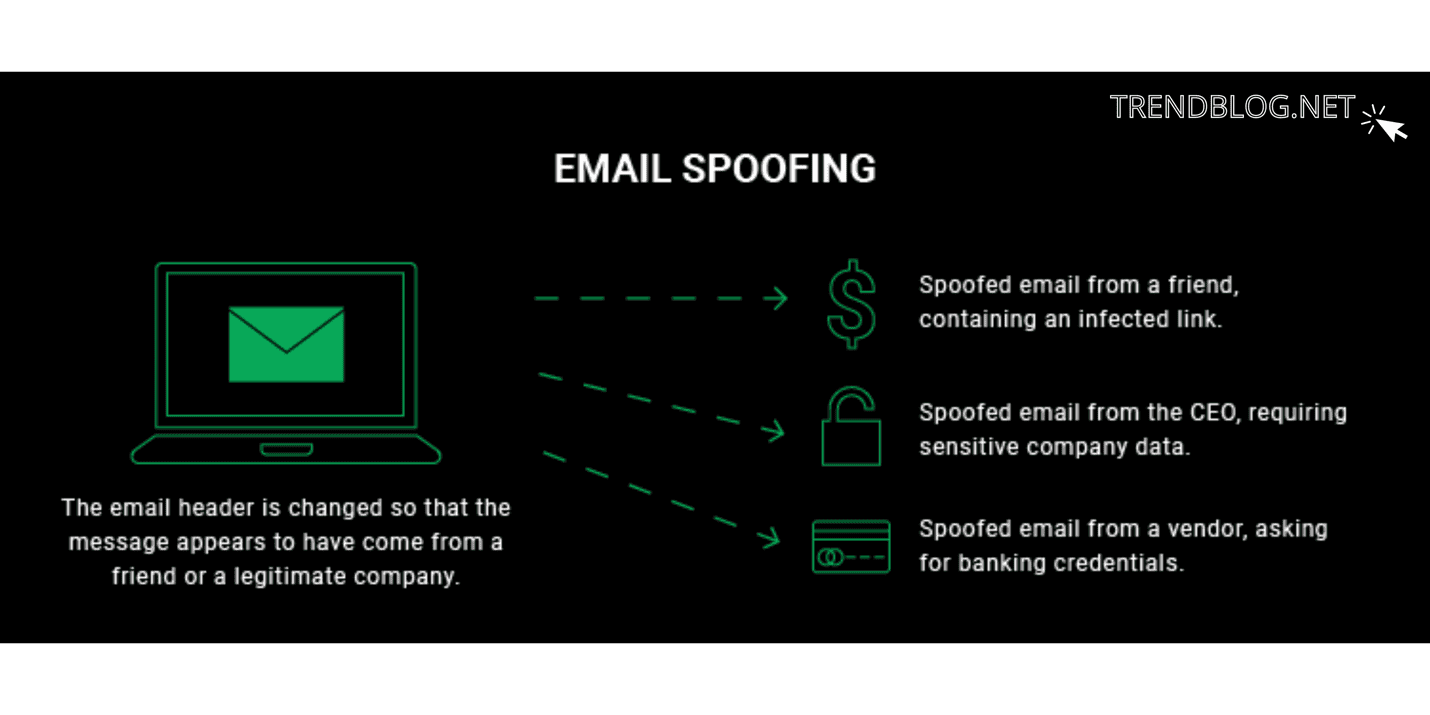
Spoofing is a common tactic used by hackers in junction with a phishing effort. Phishing is a proficiency that involves creating a phoney email account and emailing that seems to be from a credible reservoir and asks for personalized inside information. Attackers want victims to open an netmail file or hyperlink in order to download malicious software.
In subdomain impersonating, an email which looks like another account information is being utilized to misrepresent the recipient. Customerservice@facebo0k.co is an example of domains impersonator, but in a spoofing snipe, the bogus sender's domain seems real, including such customerservice@facebook.com.
When an email is a fake, how can you tell?
What distinguishes a fake email from a genuine one? Check this following netmail ID below as an example:
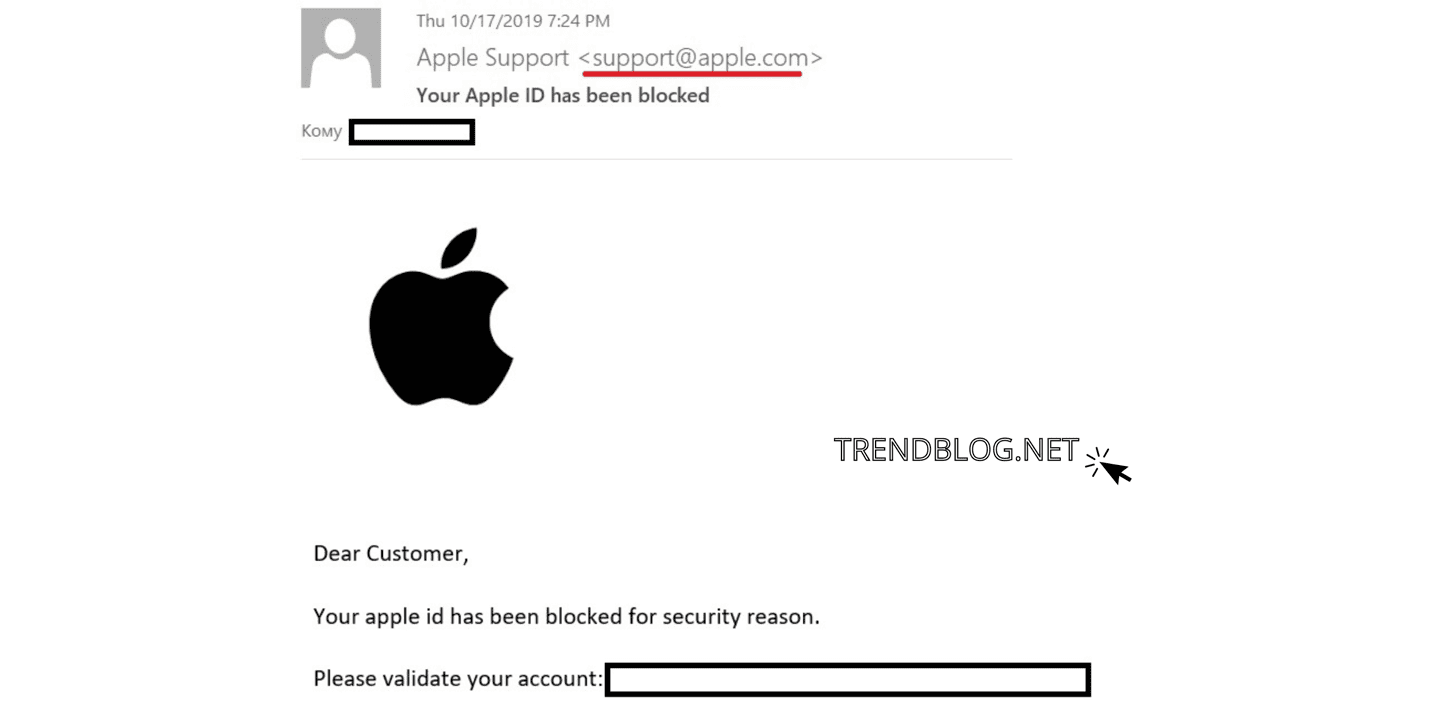
As a start, suspicious elements like the title block, recipient role destination, and attachment point to the message being a hoax. The title tag along must follow devoid of typos and weird syntax if it was from Jake's Warehouse. JakeWarehouse.com or whatsoever version of that name would make up old be used instead of blackoardinja.com as the recipient email address, and Jake's Warehouse offices would embody used as an alternative of a Vegas locating at heart the hindquarters.
There is too an confusing call to arms in the sender's body text: so what was the "Rewards Political program" and also what one must be doing to receive that a so "reward"? At that place isn't much selective information to indicate in which the nexus points unless the pass receiver is anticipating it. It's not special for spam scams to wait like this.
To sum it up, the reality that Google classified this message as folderol does not immediately rule out the possibility that it was an elaborate hoax. Purchase notifications and shipment notifications often wind up interior the spam binful because Spam detection are extravagant. Email filters, then again, are designed to observe unsuspecting receivers away of harm's agency.
Run down our clause "How To Unsubscribe From Unwanted Email Newsletters"
2021 mail faking bar strategies
Mail faking methods are improving all the time, just these are a couple things you can do to protect yourself against a catastrophic assault. The DMARC normal is one of them, as are regular employee trainings and a unified corporate identity.
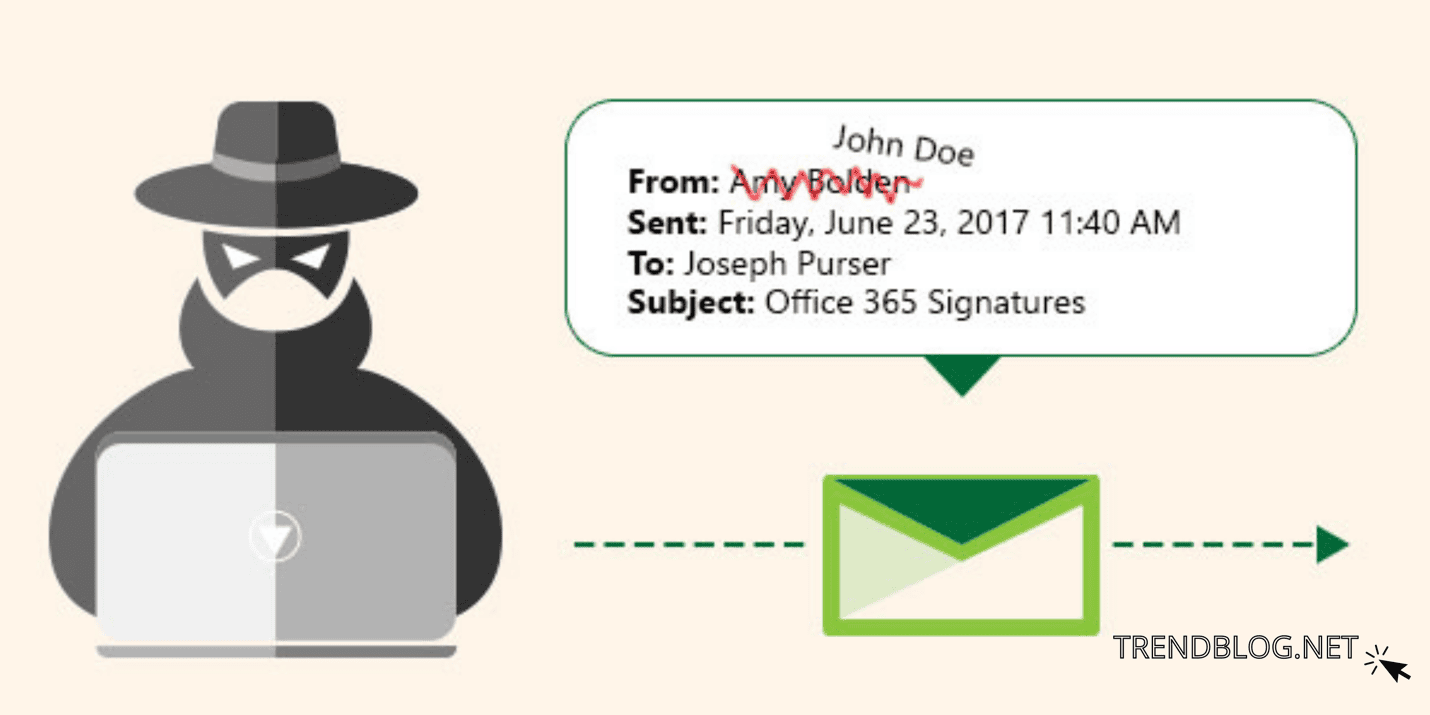
Domain-based Message Authentication, Reporting, and Conformance (DMARC) protocol
DMARC protocols are among the best powerful anti-email faking protections available nowadays. Authentication methods such as Subscriber Regulatory Fabric and Domains Credentials Identification E-mail are enabled by this customizable dominate netmail certificate chemical mechanism. As a ensue, DMARC can prevent your company's domains from becoming abused. Additionally, settings are configured to identify forgeries of the recipient identification, ensuring that emails are upcoming from the correct source.
Employee Breeding and Development
Employee training is an important part of any security effort to prevent assaults from getting past times the field of study barriers. Per year, suspend some time to educate your personnel the differences 'tween a valid email and one that is faked. After that, do review checks to give away whether anybody else has been compromised past a spam email. So, when a counterfeit email yet arrives in your mailbox, your stave will have the cognition they need to respond effectively.
Marketing of the lin
Email spoofing whitethorn also have an effect on your clients. The more your email campaigns think over the real you, the more difficult it bequeath be for mortal to pass them off every bit your firm. It's important that your inbox selling matches the look after and design of the website, fb Thomas Nelson Page, and publications. Users leave be able to tell a genuine message from a faked one whether information technology's from your organisation if it seems associate.
Source: https://trendblog.net/email-spoofing/
Posted by: corkerthlent.blogspot.com

0 Response to "Email Spoofing – What Is It? | Its Distinction From Phishing, Etc and Much More - corkerthlent"
Post a Comment